Rapid Zero Trust Deployment : 8-WK Implementation
Maureen Data Systems
The purpose and objectives of this engagement are to develop a Zero Trust Implementation Strategy
The purpose and objectives of this engagement are to develop a Zero Trust Implementation Strategy
The best starting point for deploying a “never trust, always verify” security model
Zero Trust security models have emerged as a better alternative to traditional perimeter-based defenses, especially given the shift to remote work and expansion of the attack surface.
The objectives of this engagement are to develop a Zero Trust Implementation Strategy and deployment of Zero Trust foundation security controls such as Azure AD, Intune, Conditional, and M365 security solutions.
Phase 1: Development of Zero Trust Implementation Strategy and Maturity
• People
o Zero Trust user experience balancing productivity and security
o Adoption and change management for modernizing security
o Security awareness training
• Process
o Zero Trust Adoption and change management strategy for modernizing security
o Security and Compliance risk remediation alignment process
o End-to-end security risk mitigation for cloud and business management
o Work from anywhere on any device security process
o Identity onboarding/offboarding and governance management
• Technology
o Advance conditional access using AAD, MEM, MCAS, Defender for Identity
o Privileged account management using Azure PIM / PAM
o Device security and management using MEM Intune, Defender for endpoint
o Data protection and security using MIP, MCAS, and Azure Purview
Phase 2: Zero Trust Foundation Implementation
• Azure AD and governance, MFA, SSO, Defender for Identity protection
• Zero-trust Concept , Conditional Access
o Advance device and application security integrated with zero-trust
• End to end Identity governance
o MDM, MAM
• Identity compliance, and audits
• Technologies
o Primary technologies
Microsoft 365 – AAD AD, Endpoint,
Azure – AD Services, Azure security center, Azure Automation
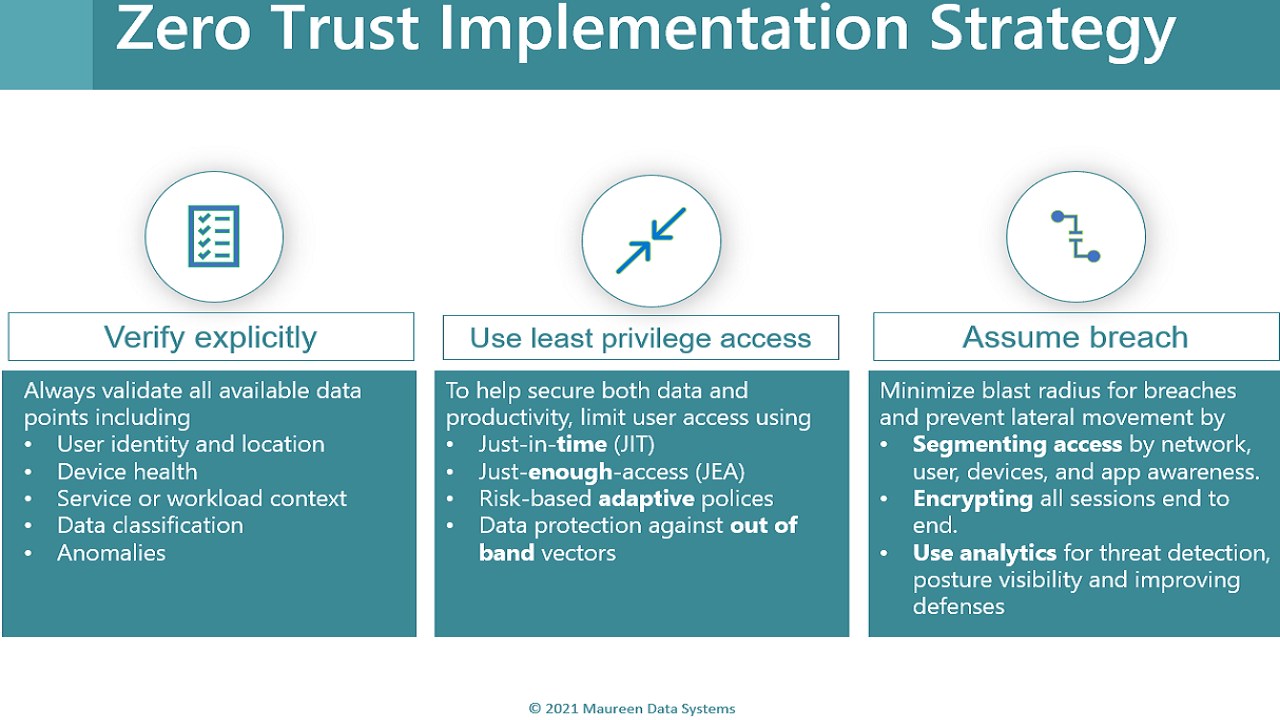
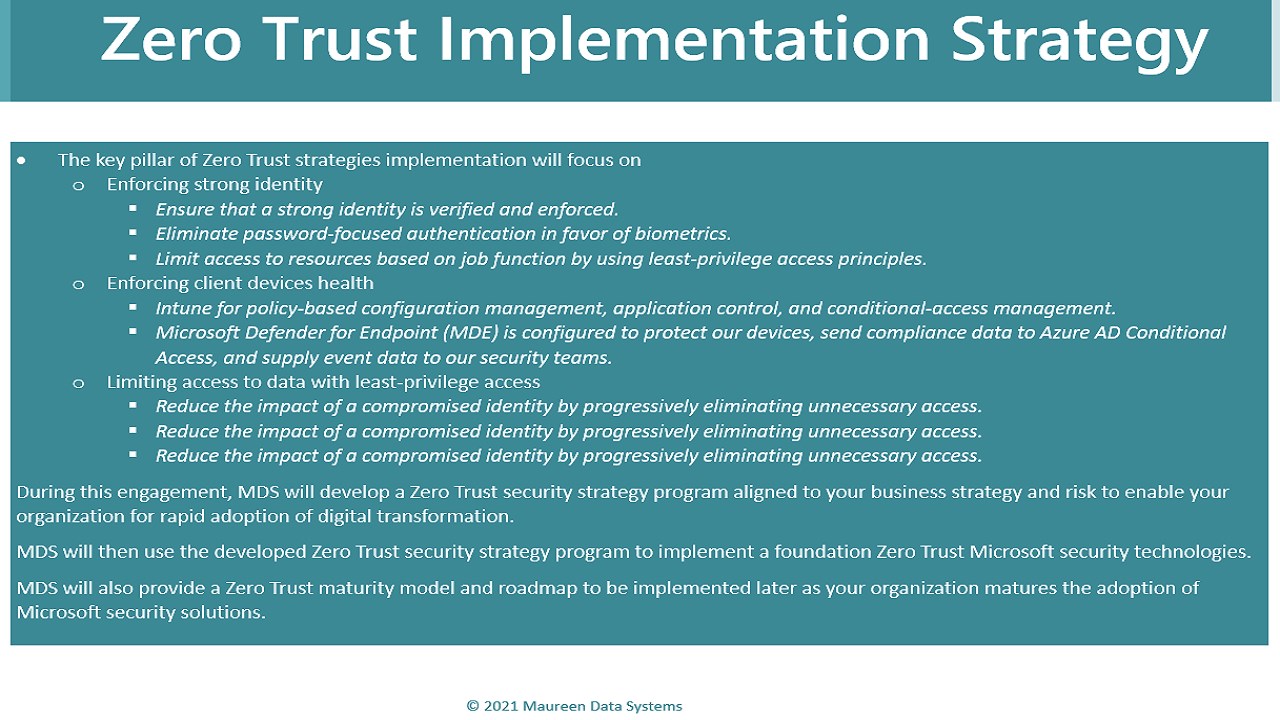
• Zero Trust policies enforcement implementation will focus on
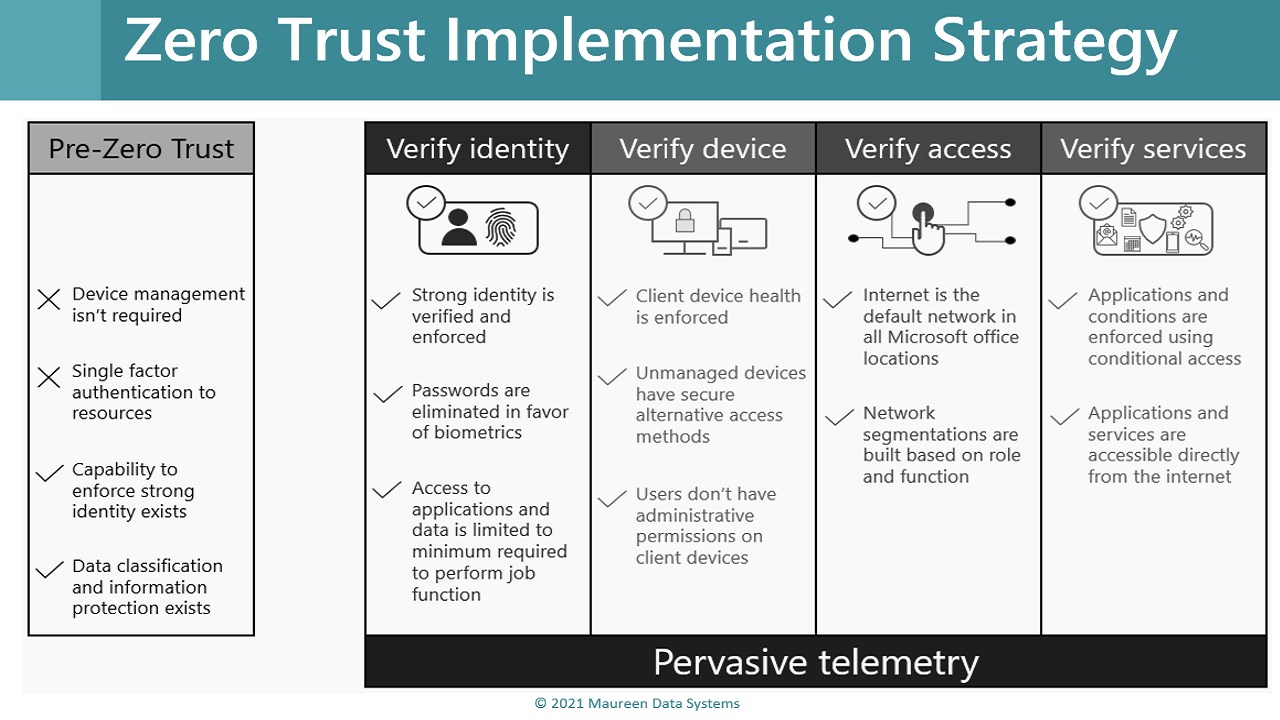
• Enforcing strong identity
• Ensure that a strong identity is verified and enforced.
• Eliminate password-focused authentication in
At a glance