Just a moment, logging you in...

Threat Protection Engagement
ISA Cybersecurity Inc.
Learn how to put next-generation Microsoft Security tools to work for you
Learn how to put next-generation Microsoft Security tools to work for you
Engagement Overview
Here’s what you can expect from this engagement:
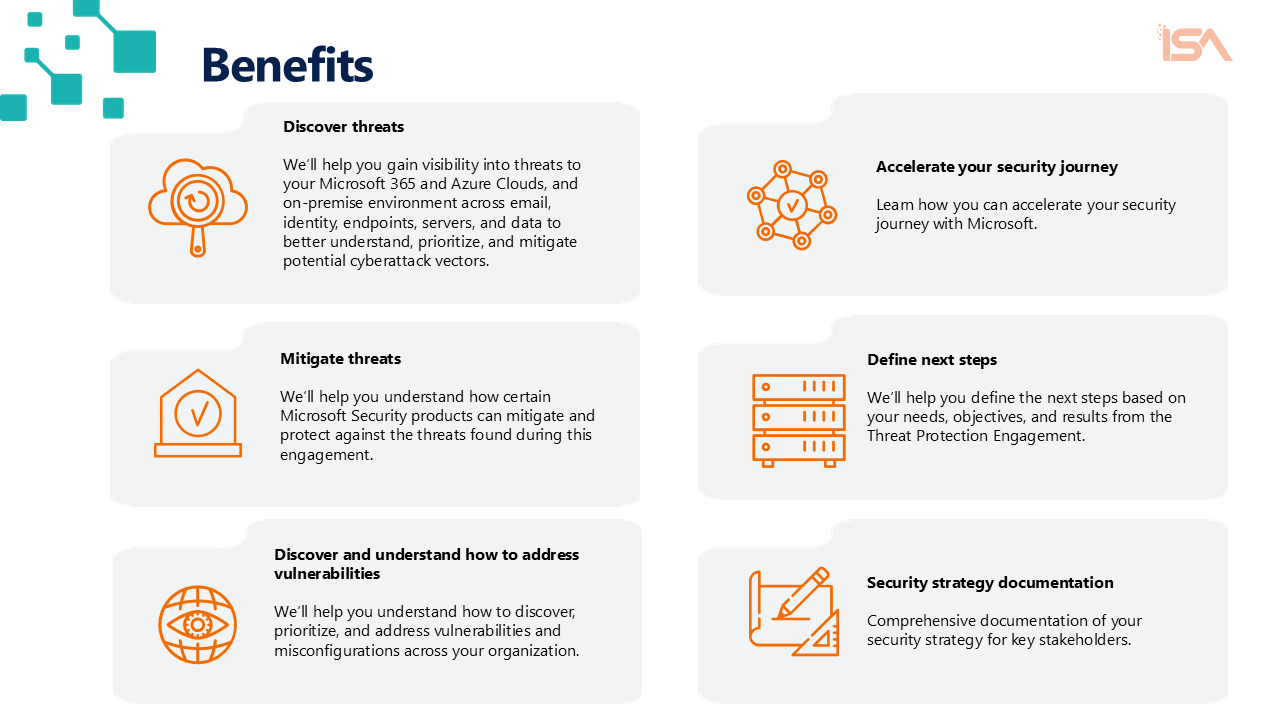
- Discover threats: Help the customer gain visibility into threats to their Microsoft 365 and Azure clouds and on-premises environment across email, identity, endpoints, servers, and data to better understand, prioritize, and mitigate potential cyberattack vectors.
- Understand how to mitigate threats: Help the customer understand how the included Microsoft Security products can help them mitigate and protect against the threats found during this engagement.
- Discover and understand how to address vulnerabilities: Help the customer understand how to discover, prioritize, and address vulnerabilities and misconfigurations across their organization.
- Accelerate the security journey: The customer will learn how to accelerate their security journey with Microsoft.
- Define next steps: The customer will work with the delivery resource to define a list of next steps based on their needs, objectives, and results from the Threat Protection Engagement.
- Security strategy documentation: Comprehensive documentation of your security strategy for key stakeholders.
Engagement Approach
The Threat Protection Engagement can be grouped into the following phases that are delivered over 5 weeks:
Pre-engagement
- Pre-engagement call
- Prepare, send, and review the Threat Protection Engagement questionnaire
Readiness (optional)
- Engagement setup
- Kick-off meeting
- Define scope
- Change management (optional)
General setup
- Mandatory and selectable module configuration
- Data collection
Threats and vulnerabilities exploration
- Threats and vulnerabilities exploration – mandatory modules and selectable modules
Results presentation
- Results presentation and next steps discussion
Engagement decommissioning
In-scope Activities for the Threat Protection Engagement:
- Deployment of Threat Protection Engagement Microsoft 365 trial licenses in the customer tenant.
- Configuration following mandatory modules and each of the included products:
- Microsoft Defender Portal
- Microsoft Defender XDR
- Cloud Identity Protection
- Entra ID Protection
- Entra Conditional Access
- Selection and configuration of at least three of the following selectable modules:
- Unified SecOps Platform
- Microsoft Sentinel
- Email Protection
- Microsoft Defender for Office 365
- Endpoint and Cloud Apps Protection
- Microsoft Defender for Endpoint
- Microsoft Defender for Cloud Apps
- Microsoft Copilot for Security Demonstration
- Remediation of potential technical issues during the deployment.
- Threat exploration to discover threats actively attacking the customer.
- Vulnerabilities exploration to discover and prioritize vulnerabilities and misconfigurations.
- Mapping discovered threats to a recommended method of mitigation.
- Demonstration of how the relevant Microsoft security products work, going through key scenarios that will help land product value and key differentiators.
- Decommissioning of configuration and licenses at the end of engagement.
Contact us today to schedule your Threat Protection Engagement.
At a glance